A recent article in CSO magazine states that nearly half of the top million websites “pose security risks”. The CSO article is referencing the State of the Web 2016 Report from Menlo Security.
To avoid these problems, we recommend three potential solutions: upgrade your NGINX software, use NGINX Amplify for configuration analysis, or move to NGINX Plus.
There are two major sources of risk cited in the article:
- Third‑party content. Many reputable sites, for example, run ads from third‑party advertising networks. Users of the reputable site are exposed to any security breaches in the third‑party advertising network, and such breaches happen frequently.
- Old software. More than 10% of the top million sites are running old software with known security vulnerabilities. The outdated software includes version 1.8 of the NGINX open source software.
If your site publishes third‑party content, you need to work with your publishing partners to solve any problems with the content they provide to you. If your site faces the problem of “old software”, or if you want to avoid this problem in the future, see the three recommended solutions below.
Update Your NGINX Software
In specific configurations, which are rarely used and not recommended by NGINX, Inc., open source version 1.8 has a specific security vulnerability. We urge NGINX users to update to the latest version at their earliest convenience. If you rely on the version of NGINX distributed by your OS vendor, you may be using a very outdated version of NGINX. For example, Debian 8+ (Jessie) comes with NGINX 1.6.2, which is over 2 years old.
We recommend that, instead, you install NGINX from our repositories with prebuilt binaries. These binaries are built for Red Hat, Ubuntu, and a variety of BSD‑based OSs.
You can choose from two branches of the software: stable and mainline. The mainline branch is where we actively develop new features, while the stable branch is only updated to fix bugs and address security vulnerabilities. Please see this blog post for details on our branching scheme.
Use NGINX Amplify
NGINX Amplify, now in public beta, includes configuration analysis. NGINX Amplify analyzes the NGINX version you have installed, notifies you of security vulnerabilities, and recommends an upgrade path.
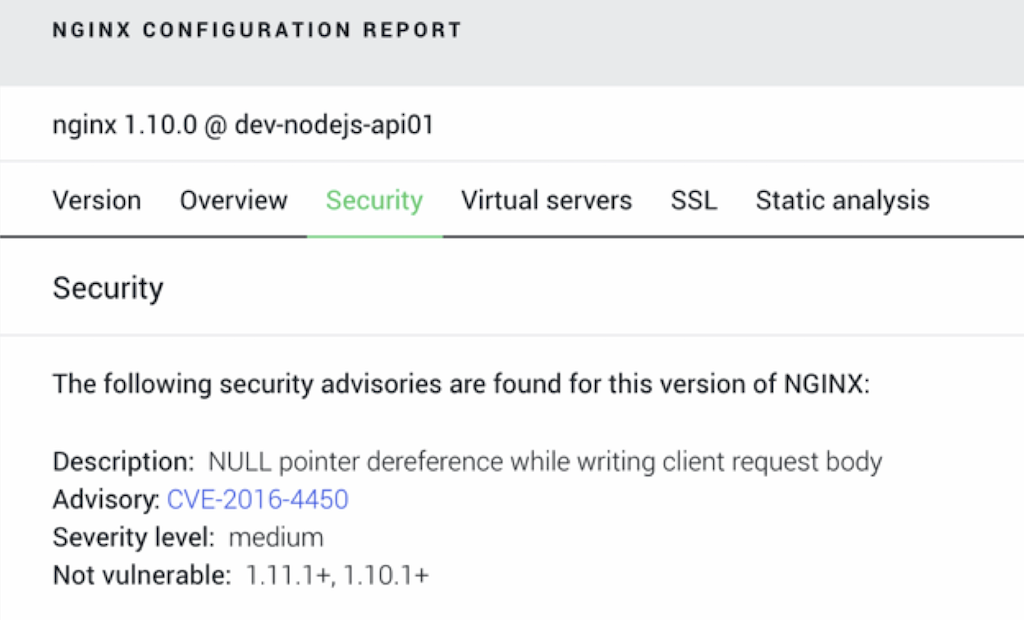
The above screenshot shows an NGINX server running version 1.10.0, which is vulnerable to CVE‑2016‑4450. In this vulnerability, an attacker can cause a crash of an NGINX worker process. NGINX Amplify suggests an upgrade to either version 1.10.1+ or 1.11.1+, which have no known security vulnerabilities.
NGINX Amplify goes well beyond identifying NGINX software versions. With it, you can find a wide range of security issues in third‑party libraries and NGINX configuration. You can then repair each issue and re‑run NGINX Amplify to confirm that you’ve addressed it.
NGINX Amplify is in public beta and it is free to sign up. Try NGINX Amplify, including its configuration analysis feature, today to ensure your NGINX deployment is up to date and free of security vulnerabilities.
Upgrade to NGINX Plus
Users of NGINX Plus, the commercial version of the (open source) NGINX software, receive advanced security notifications and regular software updates. NGINX Plus has three features that make your website less vulnerable to security issues:
- Support, with access to NGINX, Inc. engineers. When you suspect a problem, you have expert help in diagnosing issues and preventing downtime.
- Management and monitoring capabilities. NGINX Plus includes a dashboard with real‑time monitoring and management capabilities, allowing you to respond effectively to attacks in real time.
- Advanced WAF access. NGINX Plus users have access to the NGINX Plus with ModSecurity WAF, a supported version of the industry‑leading web application firewall. The combination of protection and support gives you the ability to respond more effectively to attacks.
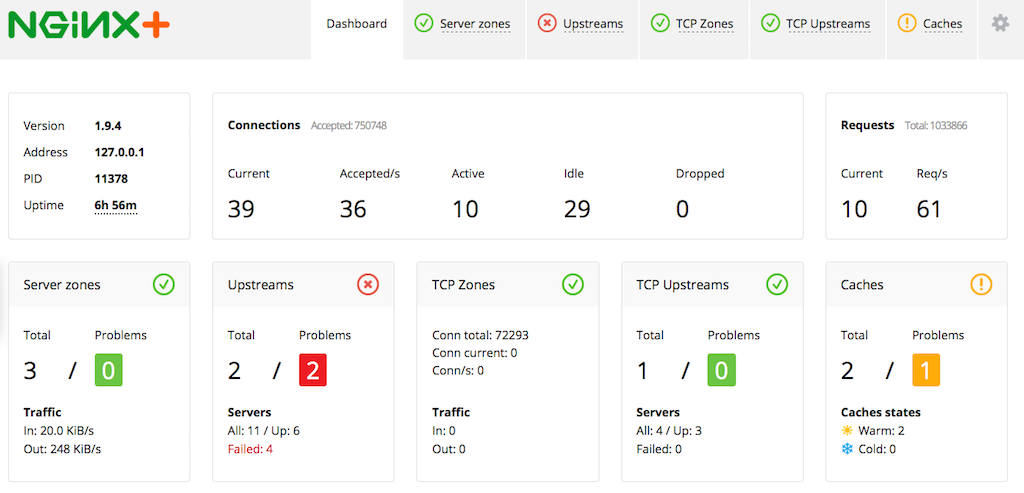
In addition, NGINX Amplify has access to additional metrics when used with NGINX Plus, giving you more ways to protect yourself.
You can download a free trial of NGINX Plus or contact Sales today.





