Since NGINX joined F5 two years ago, one of the most significant benefits to our customers has been the integration of F5’s industry‑leading security expertise into NGINX products. F5 NGINX App Protect WAF and F5 NGINX Controller App Security leverage the same web application firewall (WAF) technology as F5 Advanced WAF, F5 Silverline WAF, and other F5 security solutions. While each product has a different form factor to support particular environments, deployment scenarios, and management use cases, customers can be confident that the same known and trusted security‑enforcement engine is protecting them against the most advanced web attacks.

The shared WAF technology also means that F5 customers can retain standardized policies already approved by their Security teams as they migrate from a traditional environment that uses a product like F5 Advanced WAF to containerized and cloud environments, where NGINX App Protect WAF is a better fit. The portability of WAF policies across products makes it quick and easy for F5 and NGINX customers to ensure a strong, consistent, and compliant security posture.
When we introduced NGINX Controller App Security for the Application Delivery Module, it came with a default policy focused on protecting against the OWASP Top 10 and other threats, with minimum false positives. With Controller App Security for version 3.20 of the Application Delivery Module, you can now import your custom NGINX App Protect WAF policies and distribute them across all your managed deployments. We call this Bring Your Own NGINX App Protect WAF Policy (BYO App Protect Policy).
To learn more, read on and check out this video overview:
Maintaining Consistent WAF Policies Across the App Modernization Journey
Many of our customers with traditional application‑delivery environments start off using F5 Advanced WAF or BIG‑IP ASM. As they progress on their app modernization journey, they can leverage NGINX App Protect and NGINX Controller App Security for new apps that need a DevOps‑aligned approach to deploying WAF services.
On its own, NGINX App Protect WAF secures modern apps with features ranging from defense against the OWASP Top Ten and other advanced threats to simplified, declarative policy definition. Adopting Controller App Security to manage NGINX App Protect WAF instances has additional benefits:
- Security teams get improved out-of-the-box visibility and can provide Dev and DevOps teams with approved WAF policies and self‑service provisioning and management of NGINX App Protect WAF instances. Even better, a single Controller instance can support multiple teams.
- Dev and DevOps teams can use the Controller API and GUI they’re already familiar with to apply the approved WAF policies to their apps, without the need for in‑depth understanding of either the policies or the configuration of the NGINX App Protect WAF instances which are enforcing the policies on the data plane.
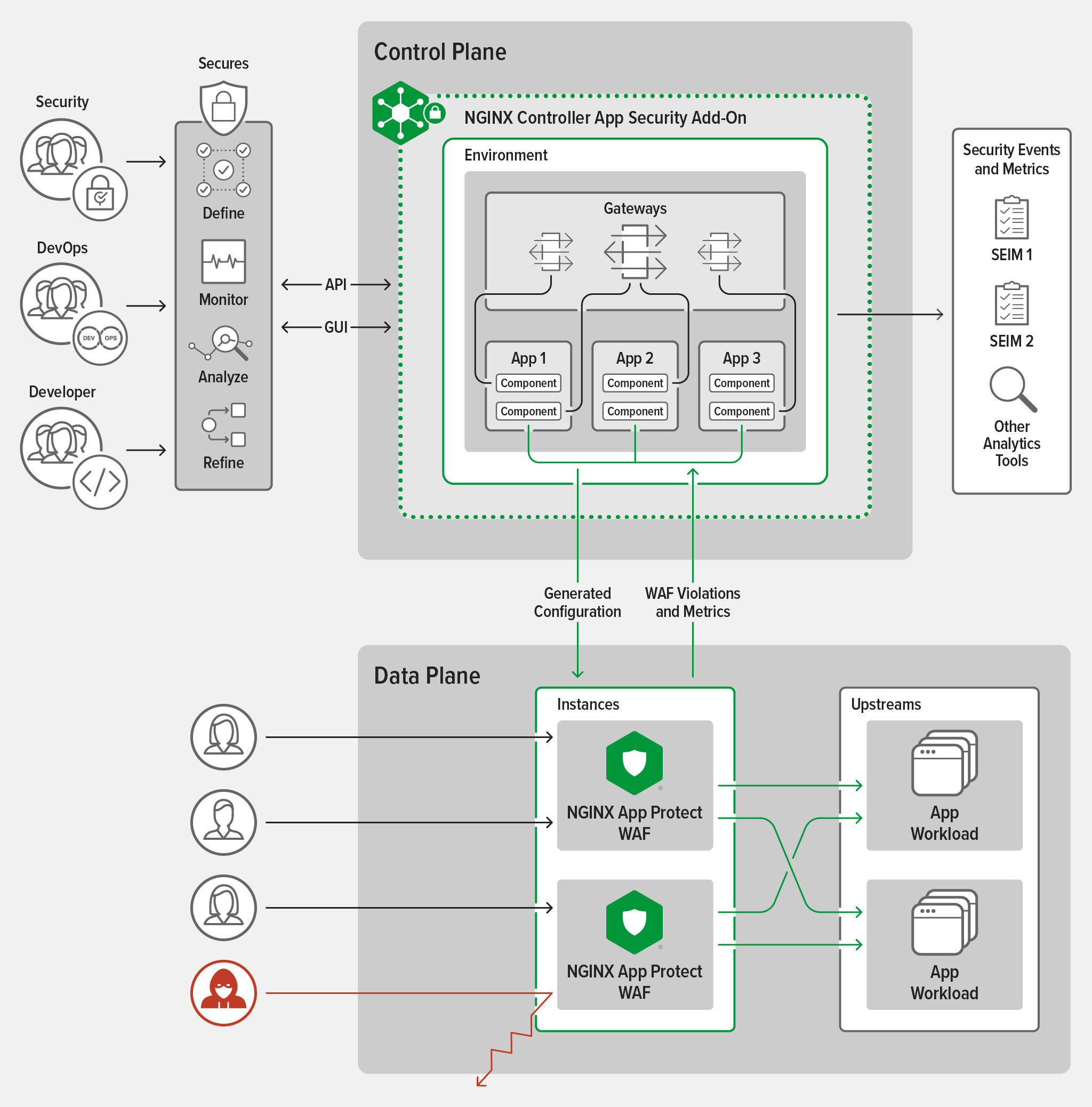
Preparing F5 WAF Policies for Controller App Security
To help you maintain consistent policies on all F5 and NGINX WAF implementations as you progress on your app modernization journey, we provide the NGINX App Protect Policy Converter. It translates F5 Advanced WAF policies (formatted in XML) to NGINX App Protect WAF policies (formatted in JSON). You can then pass the converted policies to Controller App Security as described in the next section.
Here are the steps for translating an F5 Advanced WAF policy to an NGINX App Protect WAF policy, with links to instructions.
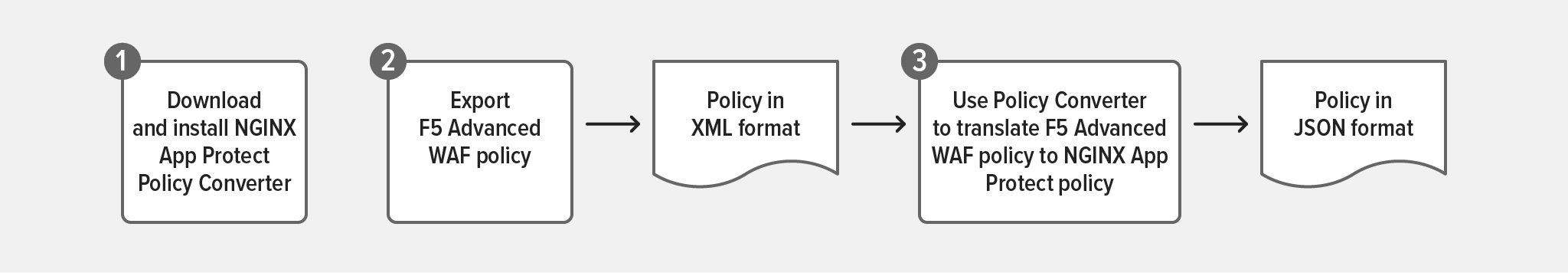
- Download and install the Docker image for NGINX App Protect Policy Converter.
- Export the F5 Advanced WAF policy (the instructions refer to “BIG‑IP ASM security policies” but also apply to F5 Advanced WAF policies).
- Convert the policy to a JSON‑formatted NGINX App Protect WAF policy.
Bringing Your NGINX App Protect WAF Policies into Controller App Security
With Controller App Security for version 3.20 of the Application Delivery Module, you can use the BYO App Protect Policy process to bring in NGINX App Protect WAF policies and distribute them across all your managed NGINX App Protect instances. The NGINX App Protect WAF policy can be a native one, or one that you converted from F5 Advanced WAF as described in the previous section.
The BYO App Protect Policy process employs a Controller object called a Security Strategy, a logical container for security‑related policies including custom NGINX App Protect WAF policies. You then reference the Security Strategy in an App to apply the associated WAF policy to the App.
For additional information about the BYO App Protect Policy process, see the product documentation.
See the instructions in the following sections for the interface of your choice:
After you complete the steps, updates to a WAF policy brought into Controller App Security using the BYO App Protect Policy process automatically propagate to all App Components that reference the associated Security Strategy.
With Controller App Security for version 3.20 of the Application Delivery Module, only WAF policies defined in a single file are supported. Support for WAF policies using external references (WAF policies represented by multiple files) is planned for a future release.
Using the API
Perform the following steps to bring a WAF policy into Controller App Security using the Controller API:
-
Pass the NGINX App Protect WAF policy with a
PUTrequest to the Security Policy endpoint:https://{{CONTROLLER_FQDN}}/api/v1/security/policies/{{policy}}with a JSON object similar to the following:
{ "metadata": { "name": "lowriskapppolicy", "displayName": "Low-Risk App Protect Policy", "description": "Corporate WAF policy for internal low-risk apps", }, "desiredState": { "content": { "policy": { "name": "lowriskapppolicy", "template": { "name": "POLICY_TEMPLATE_NGINX_BASE" }, "applicationLanguage": "utf-8", "enforcementMode": "blocking", "signatures": [ { "signatureId": 123458888, "enabled": false }, { "signatureId": 304500123, "enabled": false } ], } } } } -
Create a Security Strategy that references the WAF policy with a
PUTrequest to the Security Strategies endpoint:https://{{CONTROLLER_FQDN}}/api/v1/security/strategies/{{strategy}}with a JSON object similar to the following:
{ "metadata": { "name": "lowriskstrategy", "displayName": "Low-Risk App Strategy", "description": "Corporate strategy for internal low-risk apps", }, "desiredState": { "content": { "securityPolicyRef": "/security/policies/lowriskapppolicy" } } } -
Apply the WAF policy to an App Component (such as an app URI of an App) to reference the Security Strategy with a
PUTorPOSTrequest to the App Component endpoint:https://{{Controller_FQDN}}/api/v1/services/environments/{{env}}/apps/{{app}}/components/{{component}}with a JSON object similar to the following:
{ "metadata": { "name": "main" }, "desiredState": { "ingress": { "uris": { "/": { } }, . . . "security": { "strategyRef": { "ref": "/security/strategies/lowriskstrategy" }, "waf": { "isEnabled": true } }, . . . }
Using the GUI
Perform the following steps to bring and apply a WAF policy into Controller App Security using the Controller GUI:
-
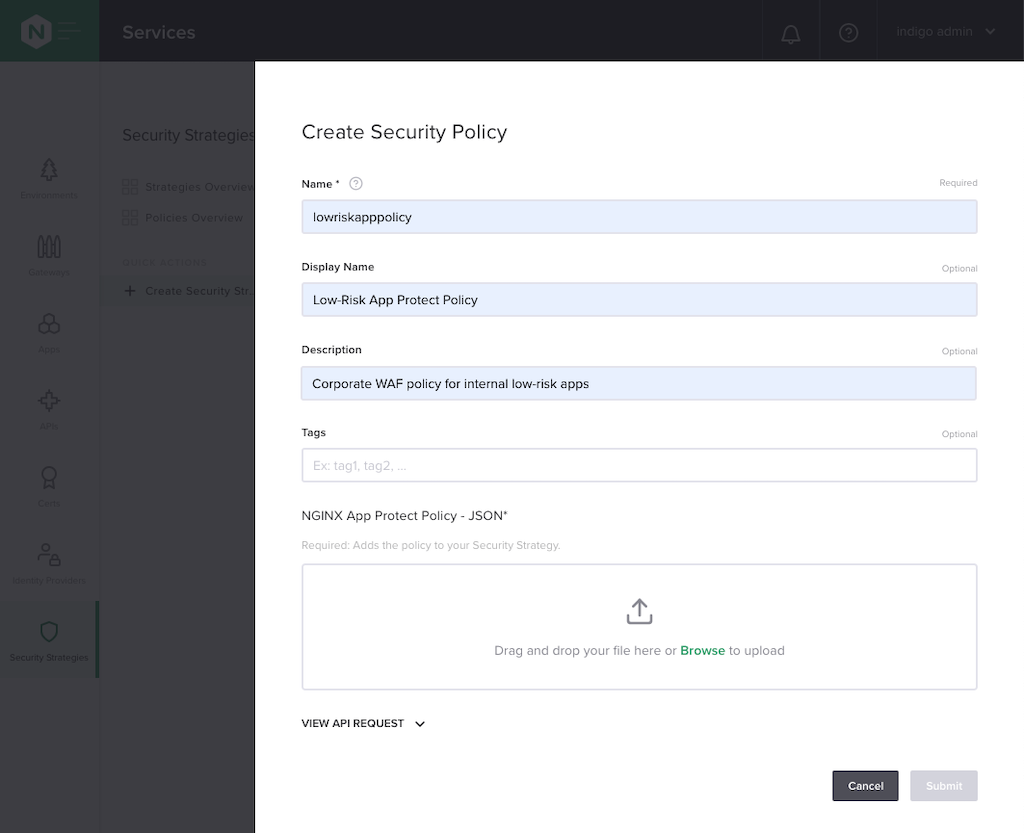
Create a Security Strategy on the Create Security Strategy page.
-
If the NGINX App Protect WAF Policy is already available in Controller, select it from the drop‑down menu in the Policy field.
If it is not already listed, click + CREATE NEW. In the Create Security Policy pop‑up window that appears, upload a file containing the JSON‑formatted NGINX App Protect WAF policy.
-
On the Edit App Component page for the App to which you’re applying the WAF policy, select the associated Security Strategy.
Sharing Policies Within NGINX Controller
After you bring a policy into Controller App Security using the BYO App Protect Policy process, it can be shared across all Apps defined in Controller, even if they are managed by different teams. Having multiple Controller App Components (or sub‑components of an App such as URIs) reference the same policies helps standardize your security posture across many apps and APIs.
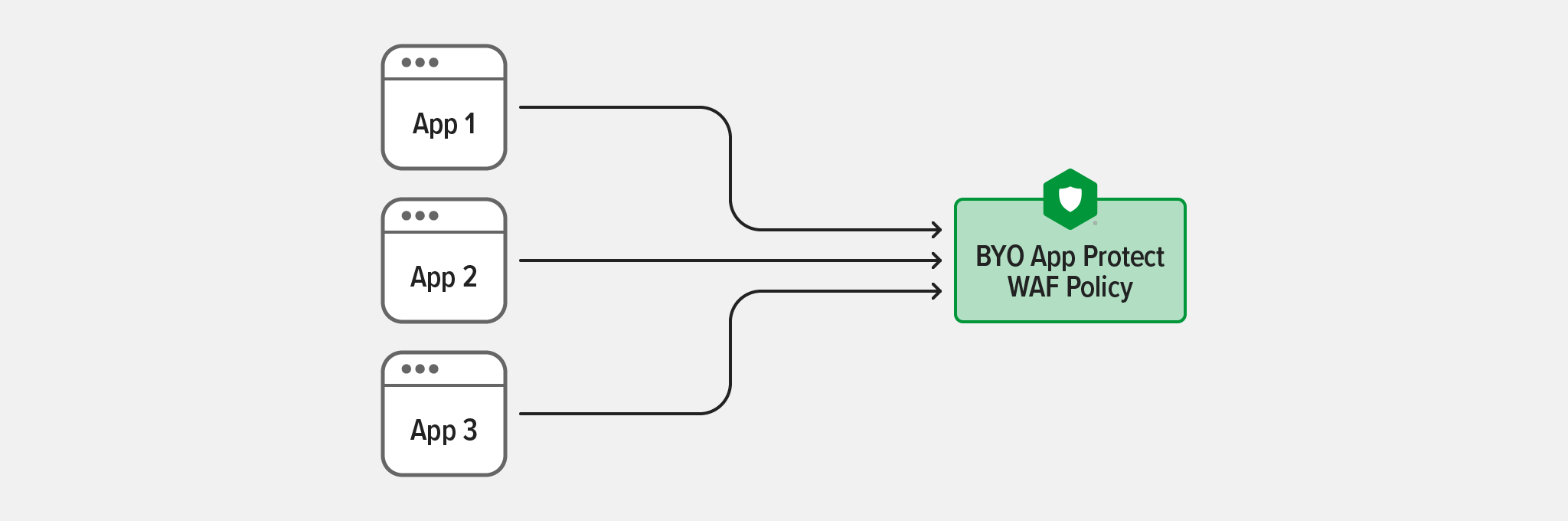
Controller centralizes management and versioning of WAF policies. When you publish a new version of a policy, it updates across all Controller App components referencing it – dramatically simplifying operations.
Summary
The F5 WAF technology platform enables portability and re‑usability of the same WAF protection policies for a standardized security posture across apps. This design philosophy also helps support all of your use cases protected by F5 and NGINX WAF solutions, making management and deployment of app security faster, easier, and more repeatable.
With Controller App Security’s BYO App Protect Policy feature (available in Controller ADM 3.20), you can now use your custom NGINX App Protect WAF policies, making it easier to protect new apps with robust, consistent, and proven policies built using NGINX App Protect WAF or F5 Advanced WAF. Best of all, with BYO App Protect Policy and Controller App Security, a single vetted policy can be applied to many apps, greatly simplifying and streamlining policy change processes.
NGINX Controller continues to enable Security teams to provide security in a self‑service model to their app teams, thus empowering organizations with both productivity and security.
Want to try NGINX Controller App Security yourself? Start your free 30-day NGINX Controller trial today or contact us to discuss your use cases.