If you work in government or a regulated industry, you’ve no doubt heard of the Federal Information Processing Standards, perhaps better known by the acronym FIPS. FIPS is a very broad set of standards publications, but in the software industry the term usually refers to the publication specifically about cryptography, FIPS 140-2 Security Requirements for Cryptographic Modules. FIPS 140-2 is a product of the joint effort between the United States and Canada called the Cryptographic Module Validation Program. It standardizes the testing and certification of cryptographic modules that are accepted by the federal agencies of both countries for the protection of sensitive information.
FIPS 140-2 defines four security levels (1–4) which correlate to the level of protection a FIPS‑certified module must provide.
- Security Level 1 relates specifically to software cryptographic modules. It stipulates which cryptographic algorithms may be used and the self‑tests that must be conducted to verify their integrity.
- Security Levels 2–4 require different degrees of physical security, such as tamper‑evident coatings or seals, and so don’t apply to software solutions on customer‑selected hardware. These levels also require role‑based or identity‑based authentication.
Why FIPS Compliance Matters
The consequences of processing sensitive information in a non‑compliant fashion can be severe. At best, it can mean the loss of a valuable contract with an organization that requires FIPs compliance, such as the U.S. Federal government. At worst, it can lead to theft of personal information or national security documents. Although FIPS 140-2 is a North American government certification, it has become a global cryptographic baseline for:
- Numerous programs and regulations which depend in some way on FIPS 140-2 validation (including HIPAA, PCI DSS, FedRAMP, FISMA, DFARS, CMMC, DoDIN APL, Common Criteria, NSA CSfC, and HITECH)
- Regulated industries (banking, finance, critical infrastructure)
- At least 16 countries outside North America that base their cryptographic requirements on FIPS 140-2 (including Australia, Belgium, Denmark, France, Germany, Israel, Italy, Japan, Netherlands, New Zealand, Norway, Singapore, South Korea, Spain, Sweden, and United Kingdom)
Global usage, coupled with the fact that FIPS 140-2 testing provides third‑party verification that crypto operations meet a defined standard, is a basis for greater confidence that data is secure as it traverses the Internet.
Improving FIPS Compliance with NGINX Plus
To become FIPS compliant, you need to configure your operating system to run in FIPS mode. But did you know that you can still be at risk of non‑compliance, even if your operating system is in FIPS mode? By enabling FIPS mode on NGINX Plus, you can ensure the clients talking to NGINX Plus are using a strong cipher with a trusted implementation.
Configuring NGINX Plus for FIPS 140-2 Level 1 is a very simple process. NGINX Plus uses the OpenSSL cryptographic module exclusively for all operations relating to the encryption and decryption of SSL/TLS and HTTP/2 traffic. OpenSSL is not part of NGINX Plus, but instead comes bundled with the operating system. So NGINX Plus becomes compliant with FIPS 140-2 for the processing of all SSL/TLS and HTTP/2 traffic when it is running on an OS from a vendor that has obtained FIPS 140-2 Level 1 validation and the OS is running in FIPS mode.
Because we find that many customers who require FIPS compliance are using Red Hat Enterprise Linux (RHEL), we’ve written our FIPS mode instructions for a RHEL 7.4 server, which applies to both bare‑metal and containerized deployments if both the host and the container are in FIPS 140-2 mode. Equivalent instructions are available from the vendors of other Linux distributions.
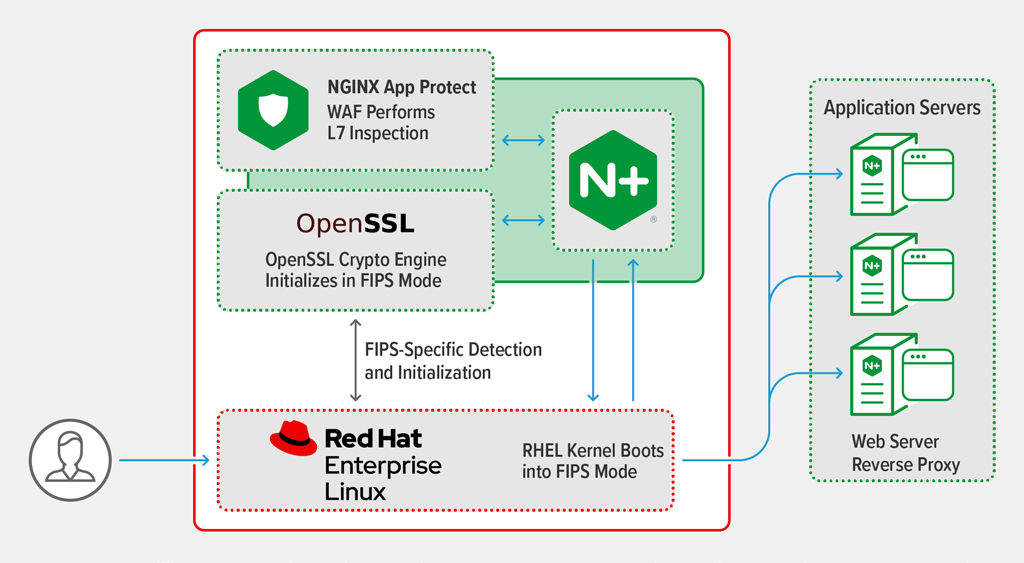
RHEL is one of our primary target operating systems, and we have a goal of testing and fully supporting NGINX Plus on all supported RHEL versions. Once you install NGINX Plus on RHEL, upgrades become the same as for any other piece of Red Hat software, meaning you can download and install updates natively within RHEL.
- Check out the NGINX Plus Technical Specifications to see which RHEL versions are currently supported. If you’re not already running NGINX Plus, start a free 30-day trial.
- Learn more about the NGINX partnership with Red Hat in our blog The Value of Red Hat + NGINX and contact us to learn how we can optimize your Red Hat ecosystem.
You can verify that your NGINX Plus instance is running in FIPS‑compliant mode using several techniques:
- The FIPS Status Check module, which is available from our repo as a supported dynamic module. When this module is loaded, it checks and logs the FIPS status when NGINX Plus starts up, and each time a worker process is initialized.
- The FIPS mode instructions mentioned above.
- A tool such as
opensslornmapto investigate the ciphers supported by NGINX Plus. Verify that ciphers not supported by FIPS are not offered by NGINX Plus. - A public scanning tool such as Qualys’s SSL Server Test to scan your public NGINX Plus instance and list the ciphers it offers.
FIPS Compliance with NGINX Open Source
NGINX tests and verifies that NGINX Plus operates correctly when it is run on a FIPS‑enabled OS that is running in FIPS mode. NGINX cannot make similar statements for NGINX Open Source, particularly for third‑party builds or when third‑party modules that implement their own crypto functions are involved. There are many pitfalls in building and validating a FIPS‑compliant solution using open source tools. Depending on your organization’s security policies, compiling and maintaining the code can be challenging or even impossible. You also run the risk of introducing a directive that can prevent FIPS certification – for example, enabling TLS 1.0 or introducing a deprecated cypher stack such as 3DES.
Finally, with some operating systems, compiling NGINX Open Source so that it operates correctly in FIPS mode requires dependencies beyond those for NGINX itself, which we therefore cannot document and which might have unintended consequences. Please review the guidance provided by your organization’s security and compliance groups to make sure that the solutions you are working with meet their requirements.
Of course, there are more differences between NGINX Plus and NGINX Open Source than just how easy it is to achieve compliance with FIPS 140-2. Explore the differences and see if NGINX Plus is right for your organization.
To try NGINX Plus, start your free 30-day trial today or contact us to discuss your use cases.





